How Trezor Suite App Enhances Crypto Security & Privacy
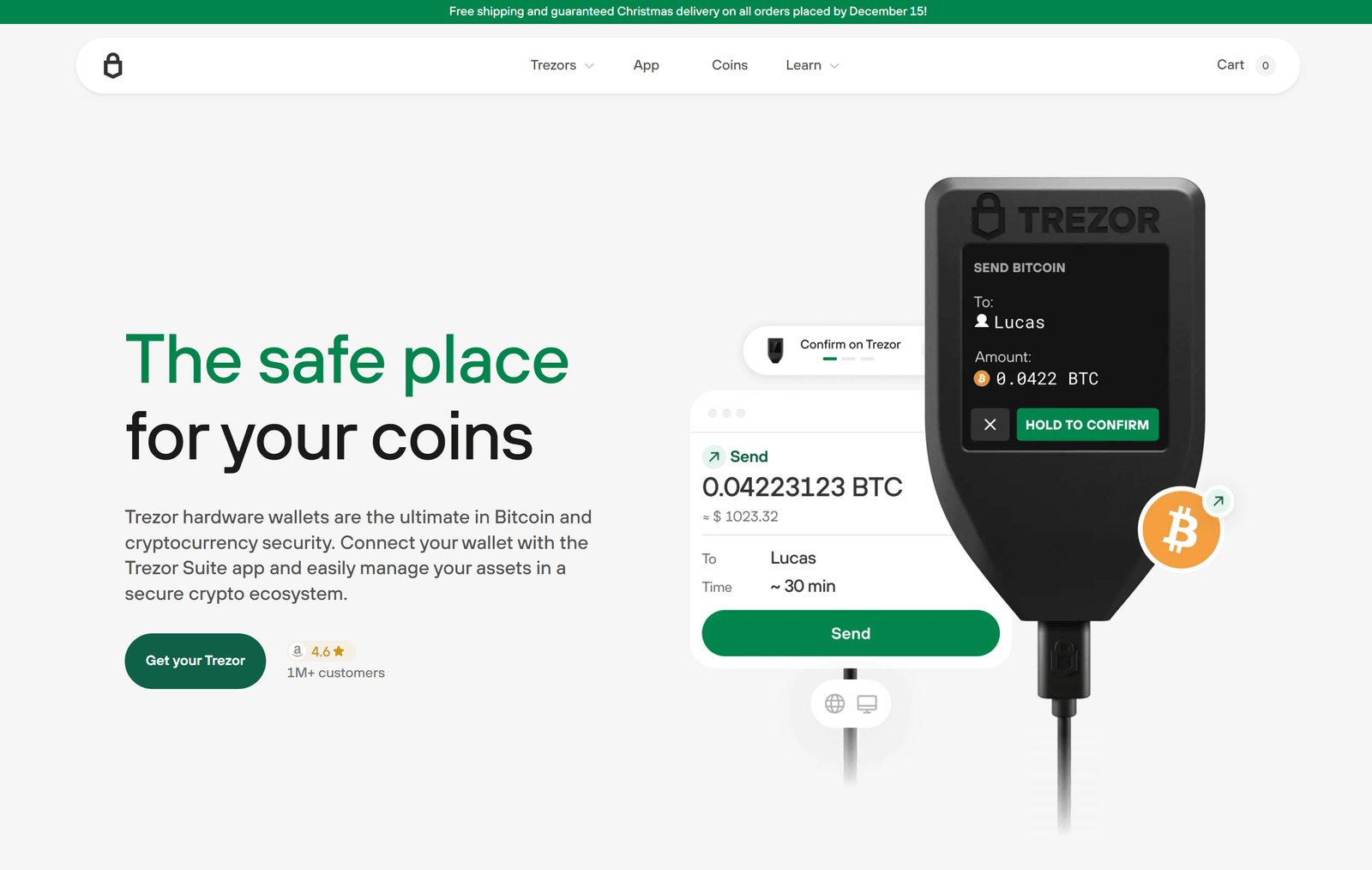
Crypto security is more important than ever in 2025, and the Trezor Suite App is at the forefront of protecting digital wealth. This blog explores how Trezor Suite’s advanced security framework ensures that your assets remain safe from online threats, malicious software, phishing attacks, and other vulnerabilities.
Hardware-Backed Protection
Unlike software wallets, Trezor Suite works in harmony with Trezor hardware devices. This means:
- Private keys never leave your hardware wallet.
- Transactions must be physically approved on your device.
- Malware cannot sign transactions on your behalf.
Even if your computer is compromised, your crypto stays protected.
Multi-Layer Security Protocols
Trezor Suite App includes:
- PIN protection
- Passphrase encryption
- Secure recovery seed management
- Firmware verification
- Anti-phishing checks
These layers ensure complete security from end to end.
Privacy Through Tor Integration
Users can enable Tor Mode to route traffic anonymously. This prevents:
- IP tracking
- Location leakage
- Monitoring by third parties
Tor protects your metadata and ensures anonymous transactions.
Secure Built-In Exchange
Unlike typical online exchanges, Trezor Suite ensures that swap operations remain private and secure since keys never touch the internet.
Hidden Wallets for Extra Protection
With hidden wallets, you can store assets using a secret passphrase. Even if someone forces you to unlock your device, hidden wallets remain inaccessible unless the correct passphrase is entered.
Conclusion
For users who take privacy and security seriously, few tools come close to the Trezor Suite App. The app continues to innovate and set new standards for crypto protection.